Privacy Policy
“Customer Privacy Protection” is emphasized at Chunghwa Telecom in compliance with “Personal Data Protection Act” and “Regulations Governing Non-governmental Personal Data Security Protection Designated by the National Communications Commission.” Privacy Policy has been stipulated, along with rigorous privacy security management and protection measures. The scope of application encompasses all groups, branch offices, subsidiaries, and suppliers of the Company.
Internally, we have formulated “Data Governance Policy” and data governance management regulations across six dimensions. Data definition consistency, data quality, and employee data literacy are enhanced by streamlining operational standards and processes. Hence, we ensure that data protection, data compliance, data quality, data operations and maintenance, data tools, and data access and sharing all meet the corporate and regulatory requirements.
Prior to any business promotion, risk assessment will be conducted to examine and ensure data access in compliance with the regulatory requirements and to check if data protection mechanisms are in place to avoid risks in data processing. To take it further in terms of “customer privacy protection,” we proactively introduced ISO 27701 system to assure the effectiveness and legal compliance in the lifecycle of data.
Regarding the collection, processing, use, and protection of personal information and privacy involved in the operation, aside from compliance with government’s relevant laws and regulations, personal information is used within the defined scope of regulatory requirements and will not be disclosed to a third-party via exchange, lease or otherwise at will. Also, relevant actions are implemented in accordance with the “Privacy Protection Policy” stipulated by the Company so as to uphold the security of customer information and privacy.
➤ Check out our 《Privacy Policy》 、 《Data Governance Policy》and 《Personal Data Collection Notice》
Customer Privacy Protection Management Mechanisms
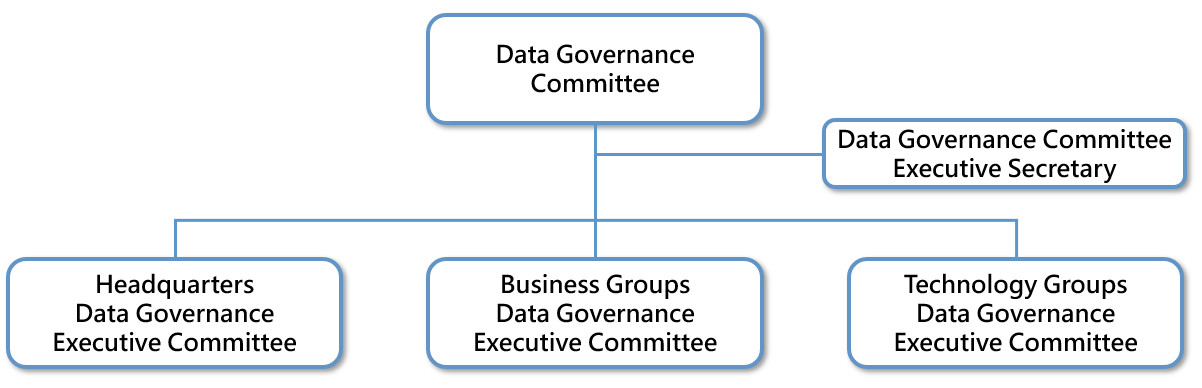
Data Governance Operational Structure and Responsibilities
| Item | Description |
|---|---|
| Data Governance Committee |
|
| Data Governance Executive Committee |
|
Privacy Protection Risk Management
| Item | Description |
|---|---|
| Group-wide risk management |
|
| Information security and privacy protection awareness training |
|
| Performance Evaluation & Disciplinary Actions |
|
| Internal audit of privacy protection |
- Headquarters: annual personal data audit organized once a year - Audit Department at Headquarters (directly under the Board of Directors): internal control audits organized each year |
| External audit of privacy protection |
|
| Enhance Supplier Security |
|
Internal System and Results
Procedures for Personal Data Incident Prevention, Report, and Response
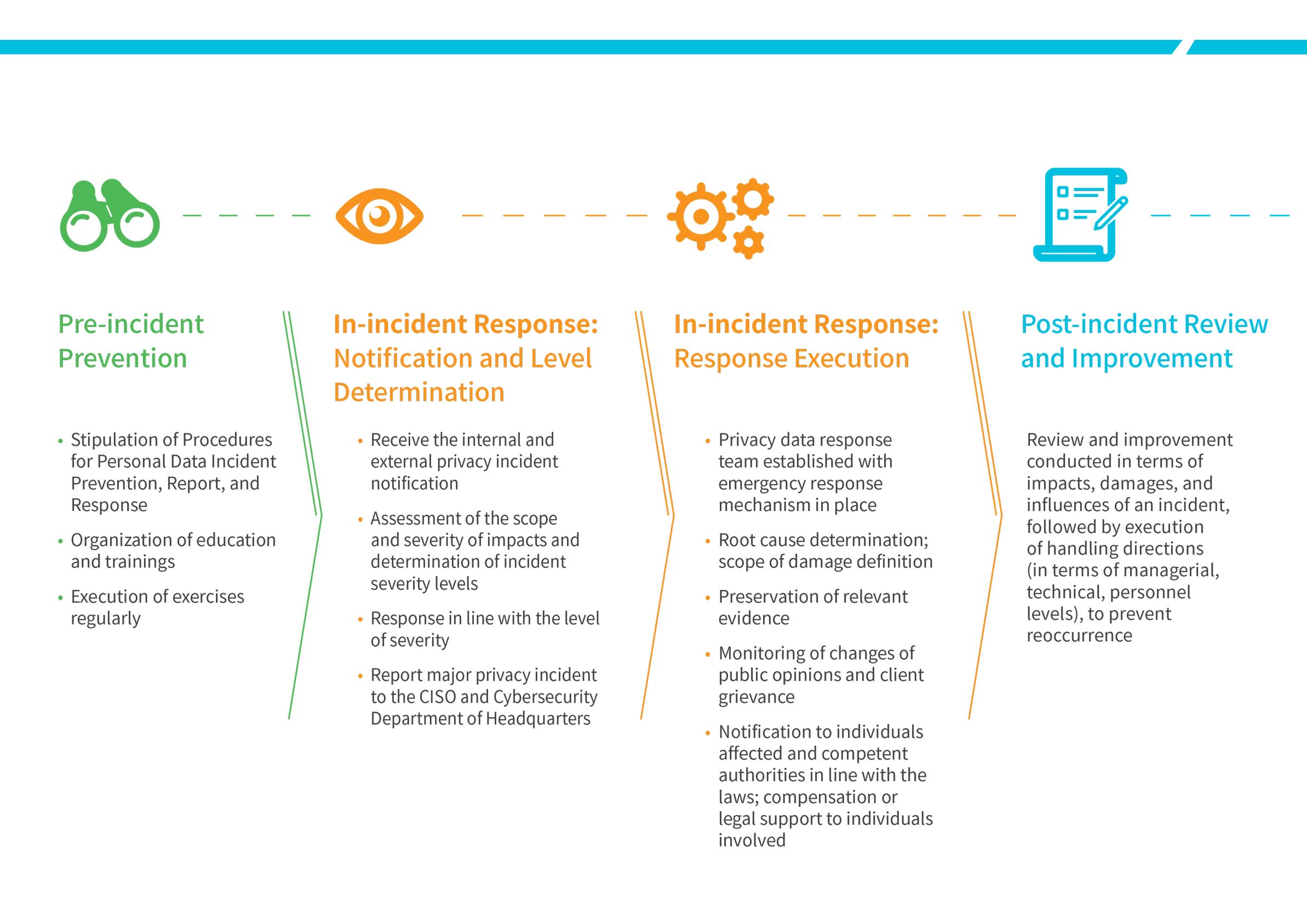
A sound mechanism of reporting, emergency response, and follow-up correction for breaches of customer privacy as well as the “Procedures for Personal Data Incident Prevention, Report, and Response” has been established at Chunghwa Telecom. With rigorous protection measures in force, we prevent any unauthorized access, disclosure, use, or tampering of personal data. Exercises are conducted on a regular basis to raise awareness and knowledge of our employees in reporting and response processes.
Upon detection of potential privacy incident, it is required to complete reporting based on the reporting list of contact in the specified periods. Should a privacy incident be verified, emergency response procedures will be set in motion immediately in line with the existing incident handling procedures to complete the emergency handling in the specified timeframes as follows:
- Assess and respond in line with the scope and severity of impacts, where a major privacy incident is to be report to the Cyber Security Department and the CISO.
- The privacy data response team is established with emergency response mechanism in place for incident investigation and analysis to determine the root cause, define scope of damage, and preserve relevant evidence of an incent.
- Changes of public opinions and client grievance are monitored to learn about the personal data illegally collected, processed, used in the incident and prevent further damage.
- Individuals affected and the competent authorities are notified in line with the laws. Where the incident has led to damage to clients’ rights, we provide compensation or legal support to the individuals involved to assist and protect our clients’ rights to the best of our ability.
- Review and improvement are conducted in terms of the impacts, damages, and influences of an incident to prevent reoccurrence.
Privacy Incidents
There were 0 “alleged information breach cases” filed via the customer hotline of Chunghwa Telecom in 2024.
Specific Data Management Mechanisms
In alignment with the major areas of Data Management Knowledge (DMBOK) of Data Management Association (DAMA), Chunghwa Telecom constructed its data governance structure of data strategy and hybrid organization and respective responsibilities. Also, the data use system throughout the Company has been established in terms of data quality, data protection, data access/sharing, data tools, data compliance, and data maintenance, so that data can be regulated, authorized, tracked, and protected. As such, it warrants an effective data governance at the Company and the subordinate institutions to achieve consistency, availability, security, and compliance in data asset management that meets international standards.
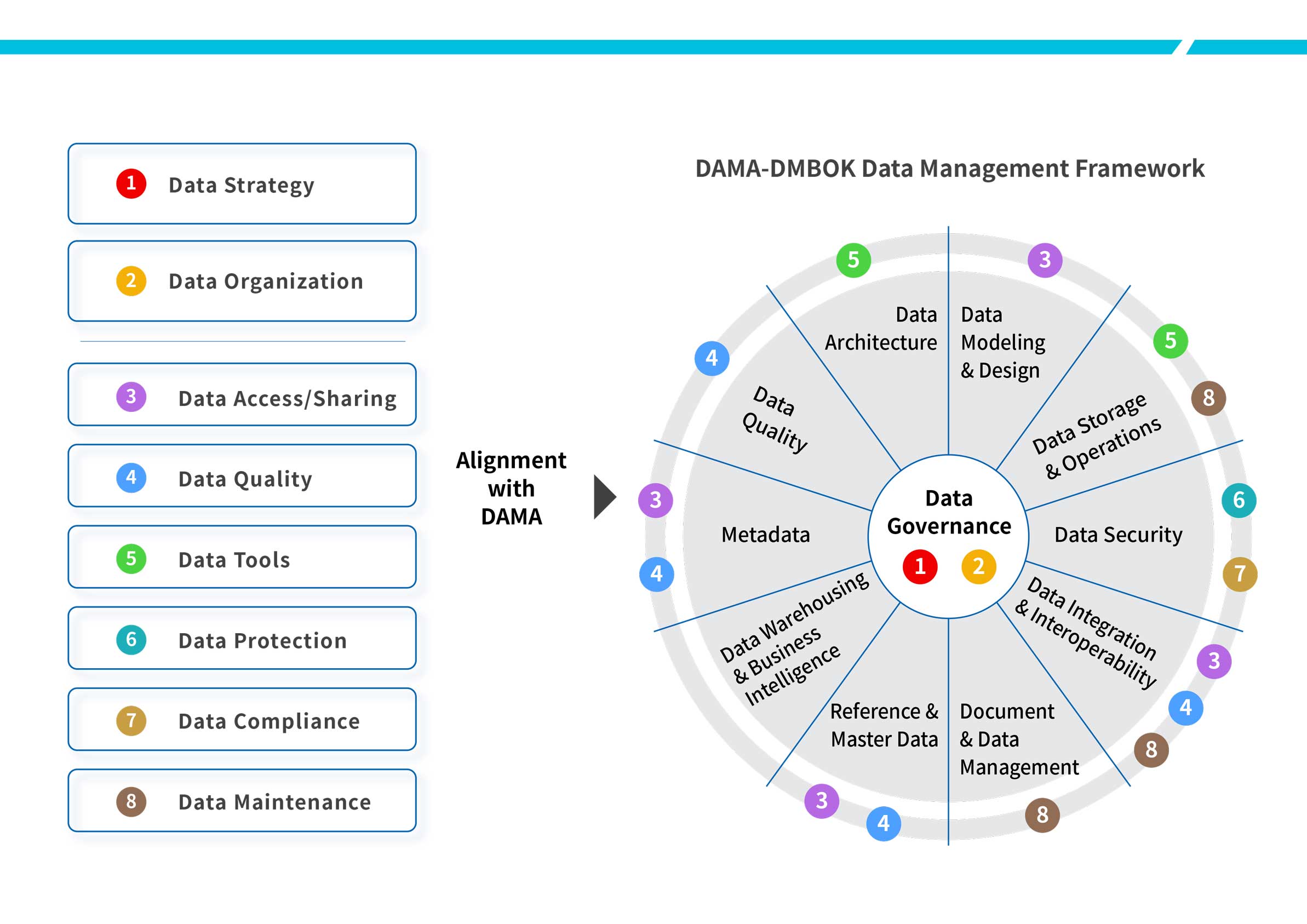
- Data Quality: Assurance of definition and monitoring of data with Chunghwa Telecom as well as maintenance of data integrity to elevate data quality
- Data Protection: Construction of data protection process with the Company to protect data in transmission and in storage; stipulation of data asset access authorization in line with data classes, and assurance in purposes of privacy protection, confidentiality, and proper access
- Data Access/Sharing: Ensuring the availability, integrity, transparency, and compliance of data, enabling effective sharing and reuse of data while reducing the risks of unauthorized access, addition, modification, and deletion of data
- Data Tools: Assurance that data governance tools used are monitored and updated, reviewed, and approved following the stipulated procedures
- Data Maintenance: Assurance of proper maintenance of databases and data assets of various businesses and logs for data maintenance operation kept
- Data Compliance: Assurance in compliance with laws and regulations at the Company and of governments to protect the data security and privacy of itself and customers




















