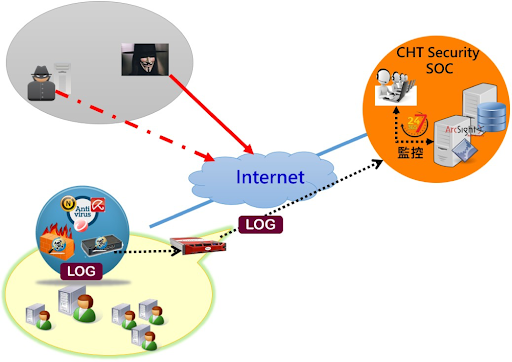
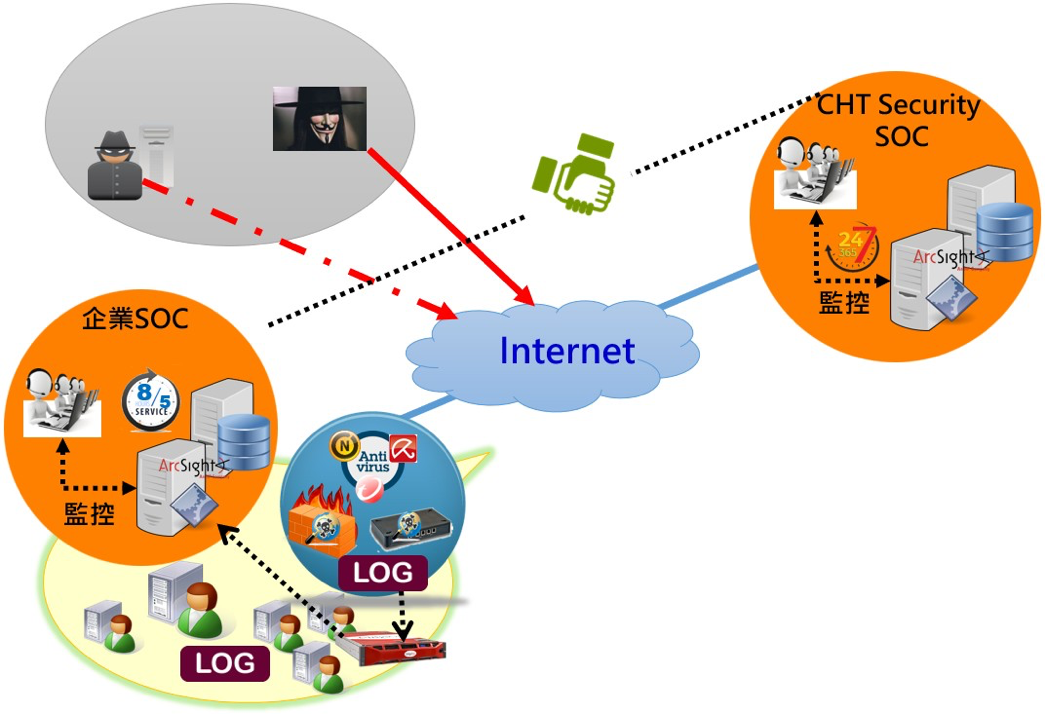
Service method
Through incorporation of the firewall, invasion prevention
systems, WAF, antivirus systems, EDR, Network
Detection&Response (NDR), DLP, and other information
security equipment, and operation system logs that are
sent back to the SOC for multiple-variate analysis, the
team can identify information security events, warnings,
and abnormal connections. If a information security event
is identified, the target is notified by email and SMS so
that timely response can be made. The information security
smart entrance website can completely and regularly
produce monitoring and statistical analysis reports so
that the customer can completely understand their
information security status.